Discounts Available For Bulk Purchases
| No. of licences per course |
% saving |
|---|---|
| 1 - 9 | - |
| 10 - 19 | 10% |
| 20 - 49 | 20% |
| 50 - 99 | 25% |
| 100 - 149 | 30% |
| 150 - 999 | 35% |
Cyber Security Course Online
£15.00
- Certified by CPD
- Audio voiceover
- Approximate course duration 1-2 hours
- Downloadable certificate on completion
- 100% online training
This online Cyber Security training course will help you to understand the potential impact of common cyber threats. It outlines safe behaviour on the Internet and also identifies what steps you can take to protect yourself and your organisation from cyber attacks.
Almost everyone spends some portion of their day online. Criminals target mobile and desktop devices and networks for illegal gains in various ways. This criminal activity, cyber-crime, is constantly changing and growing. This online course keeps you up to date with the latest developments in personal cyber security.
To stay safe online, you need to understand the main types of cyber-crime, how you can be targeted and what you can do to protect yourself.
The approximate duration of this online training course is 1 to 2 hours. However, there are no timing limitations when studying the course slides. Take as much time before your assessment as you’d like.
What is Cyber Security?
Cyber security is the application of technologies, processes, and controls to protect computers and networks from potential cyber-attacks. It aims to reduce the risk of these attacks and protect against the unauthorised exploitation of computer systems.
Sound knowledge and understanding of cyber security will help protect you against malicious attacks to access, change or delete sensitive data. Cyber security is used as a tool to prevent attacks that aim to disable or tamper with a computer system’s operations.
Why Cyber Security training is important
Did you know two in five businesses have experienced cyber security breaches or attacks in the last 12 months? Therefore, investing in employees’ knowledge and capabilities is crucial to keeping your employees and business safe from cyber threats.
To help you understand why smaller businesses are more likely to be hit with a cyber-attack, we’ve written a post in our blog section.This article on Why small businesses are at higher risk of cyber attacks outlines three reasons small businesses are more vulnerable. It also includes tips on how to improve cyber security.
In our online cyber security course, you’ll learn all the procedures to follow to avoid your business being vulnerable to the threat of a cyber-attack.
Who is Cyber Security training for?
The online cyber security course is suitable for practically anyone who accesses the internet at work. It applies to all devices with internet access, including desktop and laptop computers, tablets, and smartphones.
We have delivered training courses to companies working across many industries. Whether you work in a school, IT company, ticket office, or marketing agency – everyone would benefit greatly from being educated on cyber security.
At the end of the cyber security course, you will be able to:
- Recognise and understand the potential impact of common cyber threats.
- Outline safe behaviour on the Internet.
- Take steps to protect yourself and your organisation from cyber attacks.
When do I get my Cyber Security certificate?

After passing your online cyber security training assessment, you will be able to view, download and print your certificate.
All of our courses conform to the Continuing Professional Development (CPD) guidelines and have been accredited by the CPD Certification Service. Your certificate will include the CPD logo and therefore, you can use it to provide evidence for compliance.

How long is the certificate valid for?
i2Comply’s online cyber security course certificate won’t expire. Although there is no expiry date on the certificate, you’ll find a recommended ‘refresher’ date. Because our assessment is generated from question banks, this is the perfect course to retake and keep the knowledge fresh in later years.
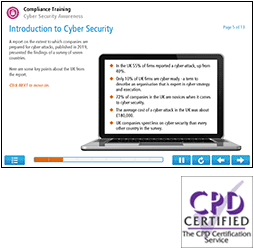
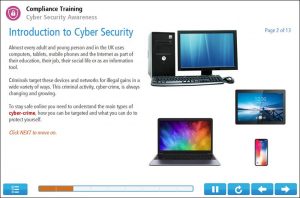
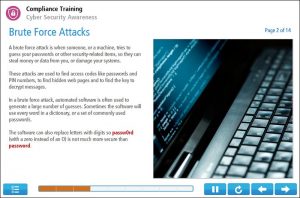
Example Screens from Cyber Security course
Below are some examples of slides you can expect from our online cyber security course. Our slides follow a format that is easy to read and retain information.
(Click on the example screens below to view)
The online course contains the following 7 topics:
1 – Introduction to Cyber Security
The first topic introduces you to cyber security. It identifies who can be a target and who commits this type of crime. You will learn about how human behaviour creates risks and specific risks associated with the Internet of Things. Lastly, the topic explains how data protection laws affect you with respect to cyber-crime.
2 – Brute Force Attacks
The second topic is about brute force attacks. You will also learn about secure passwords and how social media is used by hackers.
3 – Internet Cookies
The third topic explains why cookies are important and what they do. It also identifies risks of allowing cookies and what you can do to minimise these risks.
4 – Social Engineering Attacks
Topic 4 describes four kinds of social engineering – tailgating, phishing, baiting and chat-in-the-middle. You will also learn how to protect yourself from phishing attacks.
5 – Malware
Topic 5 describes malware – viruses, worms, Trojans, logic bombs and ransomware. It also covers ways you can defend against malware attacks.
6 – Grayware
Topic 6 explains how grayware works – For example, adware, keyloggers, bots and botnets – and how to reduce grayware on your device.
7 – Identity theft
Finally, the topic explains how criminals steal identities and what they do with them. It also identifies the warning signs that indicate you may be a victim of identity theft and explains what to do if your identity is stolen.
Cyber Security online course assessment
You can take the cyber security assessment as soon as you have finished all the topics. The assessment consists of questions taken from banks, so the assessment changes each time you do it. This means i2Comply’s online cyber security course can be used for initial training and as a refresher course.
You can attempt the test as often as you need to. Every time you do the test, you’ll receive helpful feedback which will help you learn from your mistakes.
Cyber Security online course reviews
 Before committing to purchasing an online training course, it is reassuring to first read some positive reviews. Therefore, under the page title you can find a link to our Cyber Security course reviews.
Before committing to purchasing an online training course, it is reassuring to first read some positive reviews. Therefore, under the page title you can find a link to our Cyber Security course reviews.
Our previous customers have said “Clear and concise information makes it easy to remember and enlightens you to internet security” and that “there was a lot I thought I knew but didn’t know in enough detail when it came down to it”.
Other Regulatory Compliance courses
This online cyber security course falls under our Regulatory Compliance section. Want to see what else we have to offer in this category? See the list below:
- Anti-Money Laundering Training Course
- Bribery Act 2010 Training Course
- Data Protection and the GDPR Course
- Data Protection and the GDPR (Advanced) Course
- Disability Awareness Training Course
- Equality and Diversity Awareness Course
- Freedom of Information and the Law Course
- Mental Health Awareness Course
- Modern Slavery Awareness Course
- Unconscious Bias Training Course
We also have training courses in fire safety, health and safety, food hygiene and health & social care.
Why complete the training course online?
There are many benefits of choosing an online course instead of traditional in-person training. We’ve picked out a few below:
- You can stop worrying about time limits. i2Comply courses allow you to take as long as you’d like with the study of materials.
- Because everyone receives the same slides and materials, you can be sure all staff members get consistent information about cyber security.
- You save a lot of money not having to fork out for travel expenses. Due to e-learning being fully remote, staff do not need to travel.
- The course is affordable for all businesses at just £15 per person.
- Due to the remote nature of our online cyber security course, studying can take place anywhere.
Book our online Cyber Security course today
It is easy to get started with this online Cyber Security training course. We aim to make the process as quick and easy as possible for our customers. Click ‘Add to Basket’ at the top right of the page and proceed with the payment.
Once you buy our Cyber Security course, you don’t have to start it immediately. There is no time limit on when you need to pass the assessment. Therefore, you can take advantage of this by buying course licences in bulk today and getting your staff to complete the training later in the year.
Any more questions?
We aim to provide as much information regarding our training courses as possible. Sometimes you may need more answers. Never hesitate to get in touch with a member of our team; they’ll be happy to help.
Lastly, we’d also like to point you in the direction of our help & knowledge base. We have answered a lot of previous and frequently responded to questions about accounts, licences, certificates, and payments.
£15.00
Discounts Available For Bulk Purchases
| No. of licences per course |
% saving |
|---|---|
| 1 - 9 | - |
| 10 - 19 | 10% |
| 20 - 49 | 20% |
| 50 - 99 | 25% |
| 100 - 149 | 30% |
| 150 - 999 | 35% |